DPRK IT Workers Leveraging Open Source and Freelance Platforms
On February 9, 2025, we discovered a suspicious actor within the repository of a legitimate developer. Initially, we informed the developer about the potential malicious intent of one of his active committers. This led us into a two-month-long process of discovering additional North Korean actors, “PR Spammers” and experiencing the subpar vetting process present in one of the “Pay for PR” (freelance) platforms in Web3.
First of all, this article is a call to action for any protocol or platform employing remote workers and open source contributors, especially when payments are made in cryptocurrencies and where low to no KYC is performed. Secondly, it’s a warning: avoidance of the issue by the affected platform may have consequences beyond it. By harboring DPRK IT Workers, you are allowing their credibility to grow, their future infiltration to be more effective, and you are putting developers and users outside of your platform at risk too.
Let’s start the tour of this extremely interesting activity, with twists, turns, and at least one ridiculous video call.
First Actor Discovered
The first identity we discovered belongs to a developer going by the handle 0xExp-po on GitHub. The actor’s patterns of activity fit the known DPRK IT Workers’ M.O. We collected the evidence and informed the affected repository owner, a developer working on one of Stellar’s “Build on Stellar” programs. The developer acknowledged the issue and passed the information “up the chain”. At this point in the investigation, we did not yet realize how deeply connected the whole case was to the popular Web3 freelance platform onlyDust.
List of highly unusual patterns discovered:
- Account created at
2023-12-10T13:54:11Z; however, commit history manipulation displays account history dating back to 2018. - The actor opened the usual “Spam Issues” in several organizations already associated with “Account/Activity Farming” activities.
- “Credibility building” through opening “Spam Issues” in valid organizations in exchange for badges displayed in the GitHub UI view.
- Multiple repositories with “stolen” commit history (DPRK IT Workers
git clonethe original repository and edit its commit history before pushing it to their own profiles). - Toxic following/follower patterns (checked against our internal DB).
- A strong connection to another suspicious actor we discovered later on.

Github Profile view
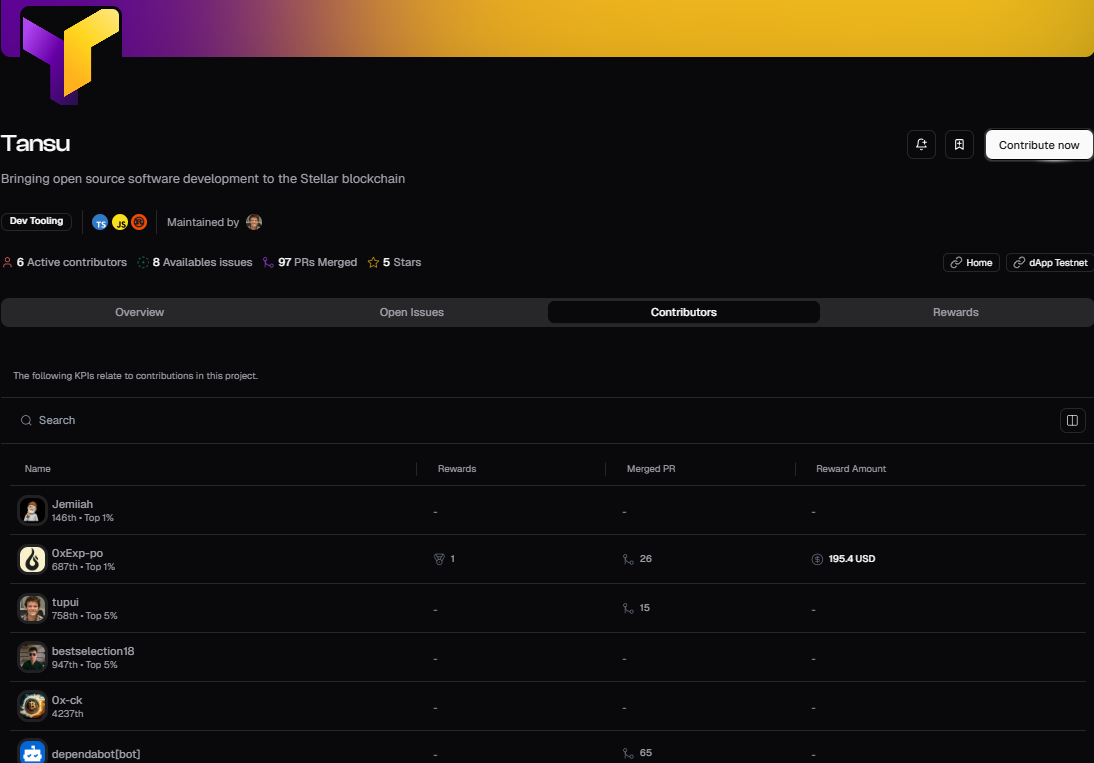
List of contributors to Tansu project on onlyDust.com
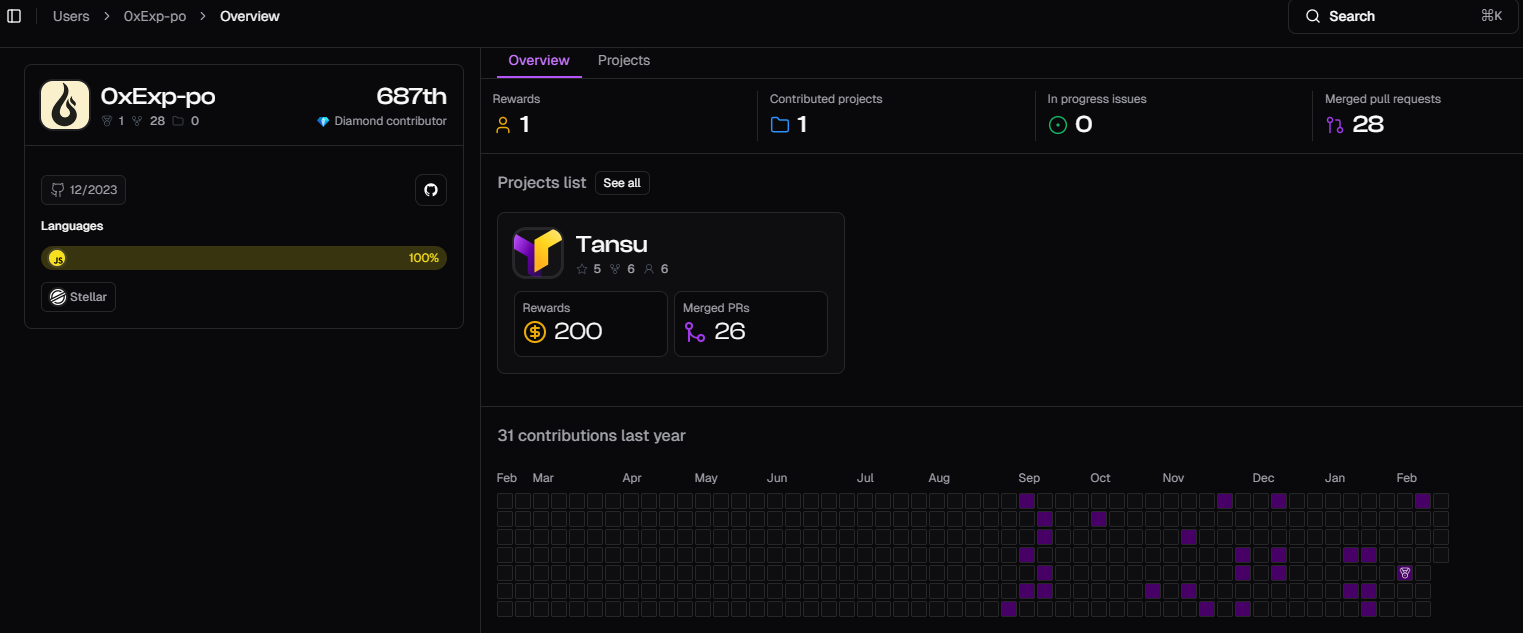
Amounts paid for work to the DPRK IT Worker (0xExp-po)
Second Actor and the Cluster Unwinds
0xExp-po led us to bestselection18. A similarly, if not more, suspicious actor who was active in the repository of the same developer. We were already aware of bestselection18 activity for some time before this investigation began, he was on a high-confidence list of suspicious actors from our past work. It was surprising to find this high-confidence actor, with a history of multiple identity rotations, in exactly the same codebase. What was more worrying was that after a deeper scan, we discovered bestselection18 was actually getting frequently paid for his contributions to multiple repositories hosted on the onlyDust platform. The cluster grew again, but it wasn’t the end of the whole case. bestselection18 was connected to multiple other DPRK IT Workers, this time outside of the onlyDust platform, but nevertheless extremely active.
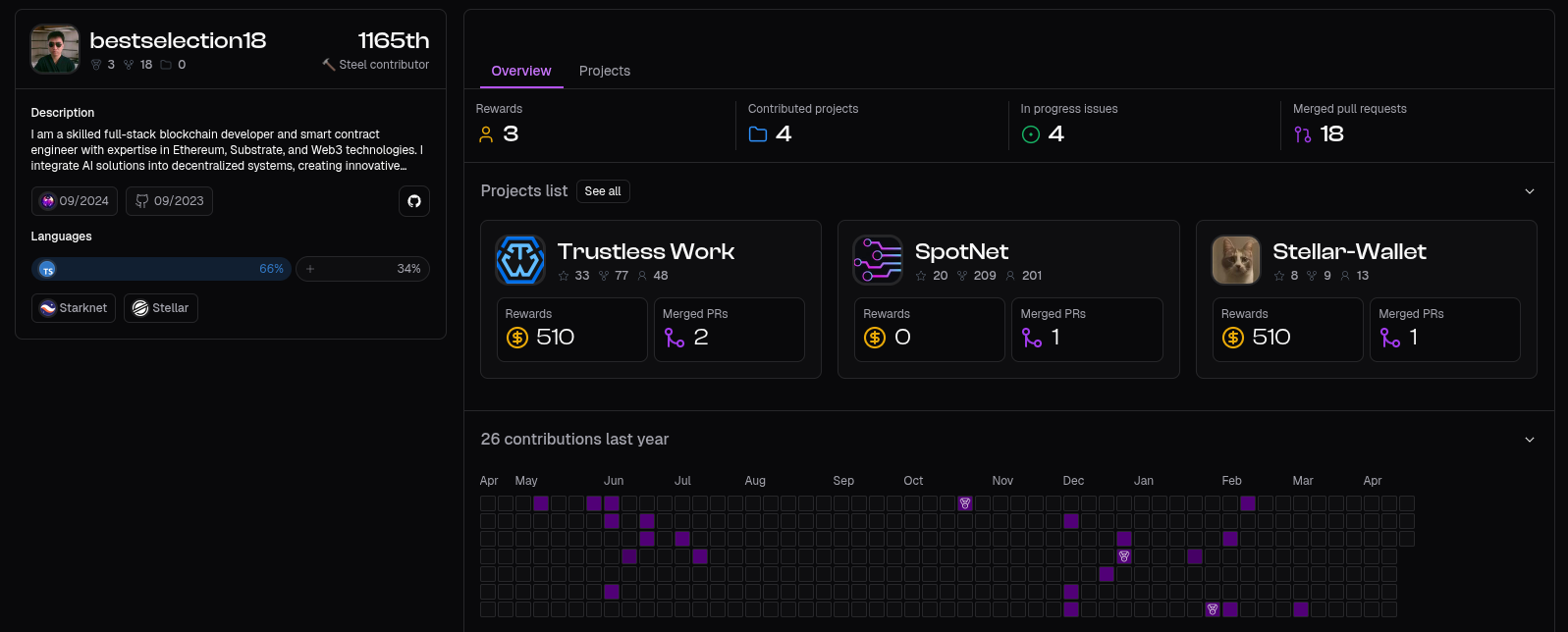
Amounts paid for work to the DPRK IT Worker (bestselection18)
List of highly unusual patterns discovered:
- The profile picture is AI-generated (most likely using the StableDiffusion model). However, even manual inspection reveals its fakeness (e.g., clothing, background, eyes visible through sunglasses).
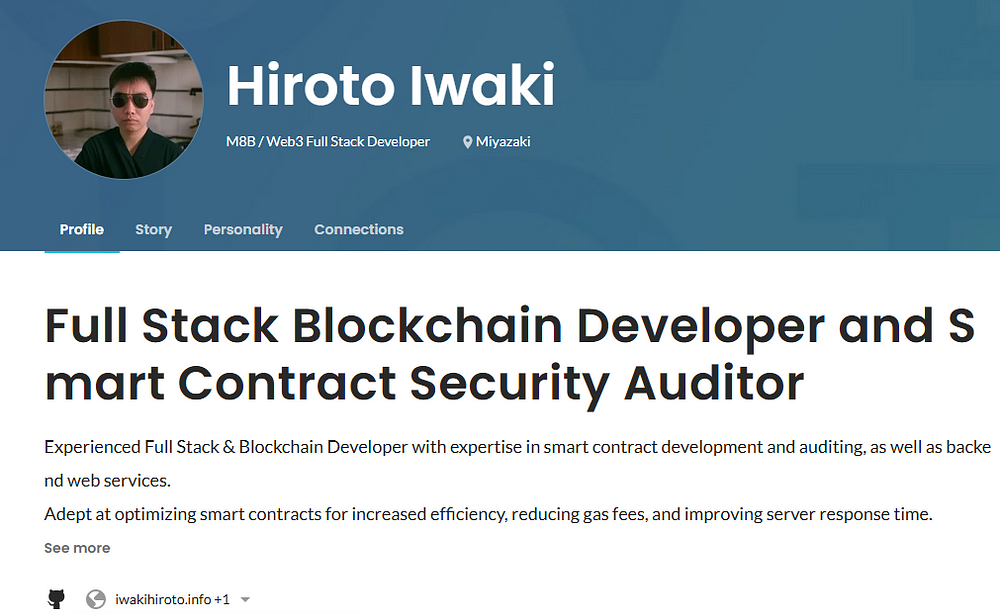
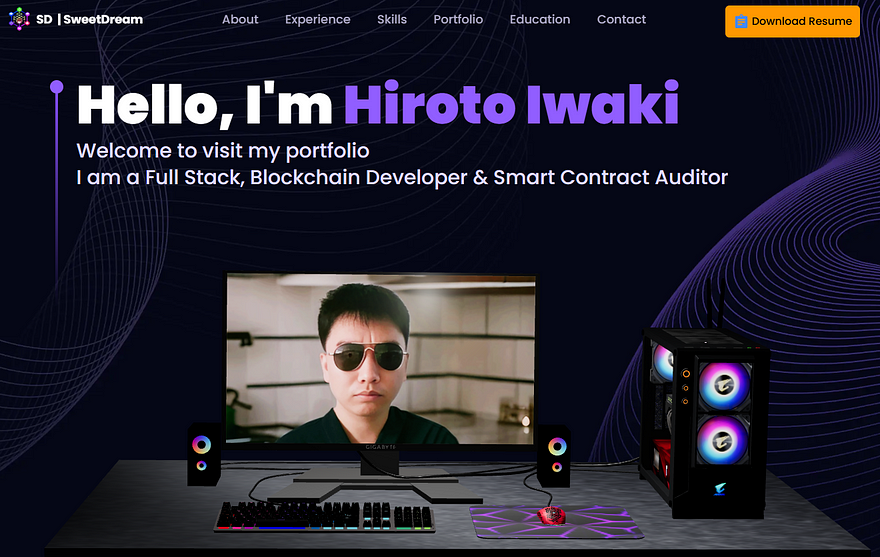
Personal website and freelancer profile of Hiroto Iwaki /
bestselection18
- Frequent identity changes—a highly unusual pattern for a non-malicious developer—were discovered by performing deep analysis of GitHub’s profile data.
bestselection18appears as the most recent and currently active identity; however, thenoahsflood908@gmail.comemailbestselection18uses was also attached to:mymiracle0118GitHub handle, currently deleted.SweetDreamGitHub handle, which appears to be connected to yet another spam account,swdreams.SmileS-777GitHub handle, currently deleted.deeplus2021GitHub handle, currently active.tranguixdevGitHub handle, currently deleted.
bestselection18/Automation-botprovides many clues as to how many “fake identities” the actor manages. The repository served as some sort of automation project for operating multiple personas, interesting on its own and not the first example of DPRK IT Workers trying to automate parts of their job.
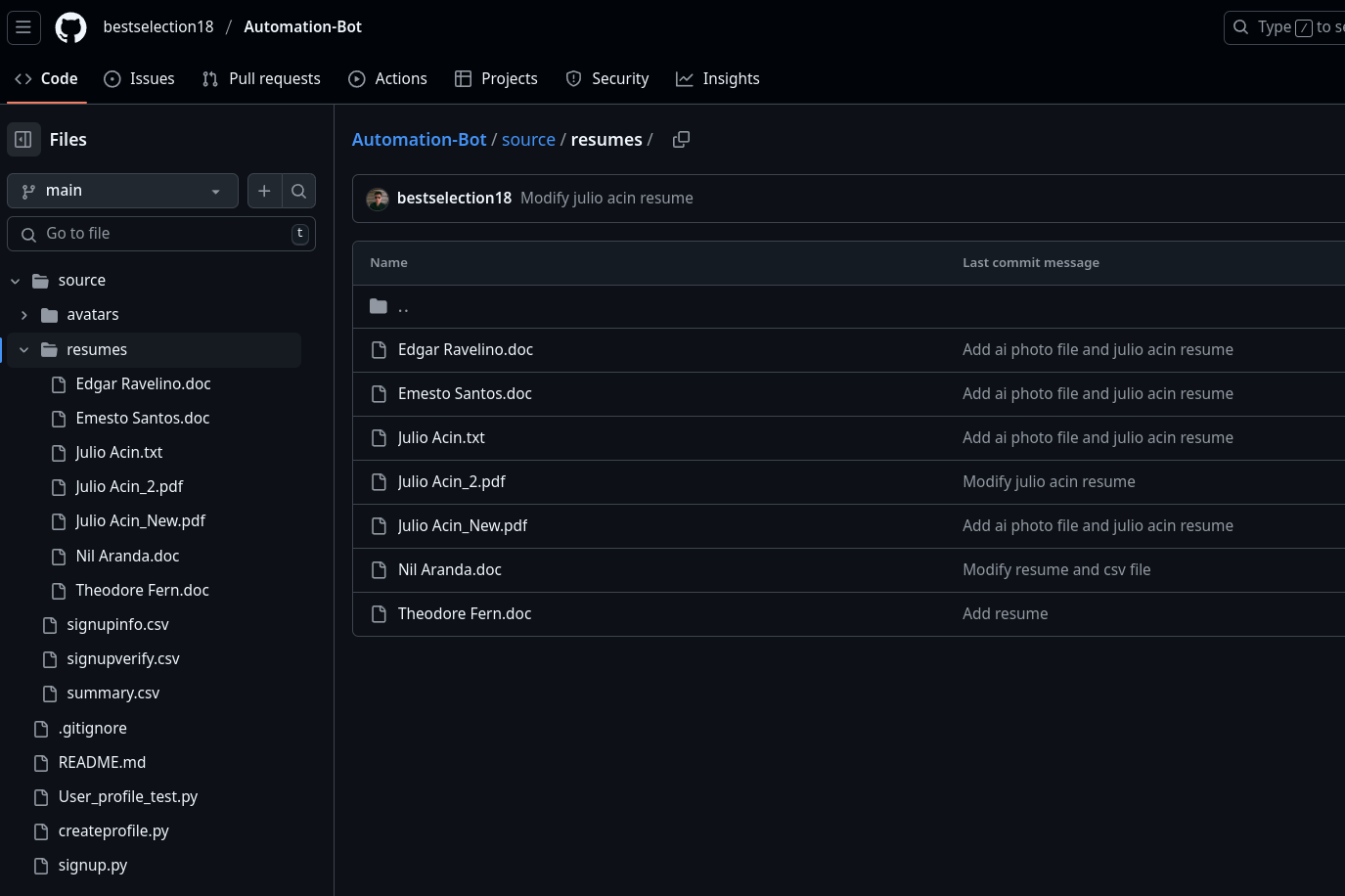
DPRK IT workers ingeniuity - An attempt at automating multiple fake identities
- We also tracked identity conflicts outside of GitHub commit data, including:
- The email
noahsflood908@gmail.comwas associated with multiple identities in several CVs. The GitHub accounttoptalhookused the same email in his portfolio.toptalhookis another suspicious / threat actor account, although this account is out of scope for this investigation.
- The email
- The identity of
Hiroto Iwakiusing the GitHub handlemymiracle0118working on Stellar-Metamask project, through BuildOnStellar program was found to be connected to the legitimate developerpaulfears, a lead maintainer of the project awared $71.0K to develop the “Stellar Integration on Metamask”.paulfearsrefers to certain developments that should be carried out with the “Japanese Team”. Given that many of these accounts are identified as Japanese, it’s possible that more threat actors were involved.
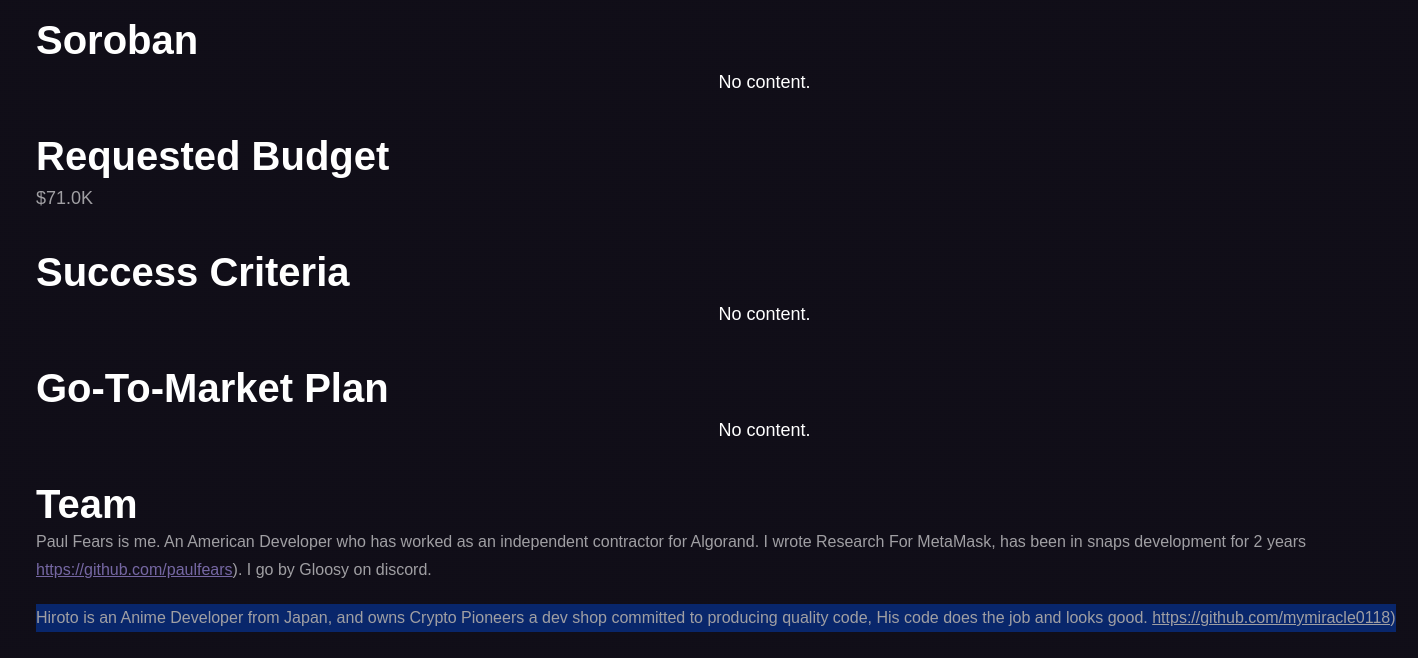
DPRK IT Worker introduced as part of the “Japanese Team”, together with his “dev shop”.
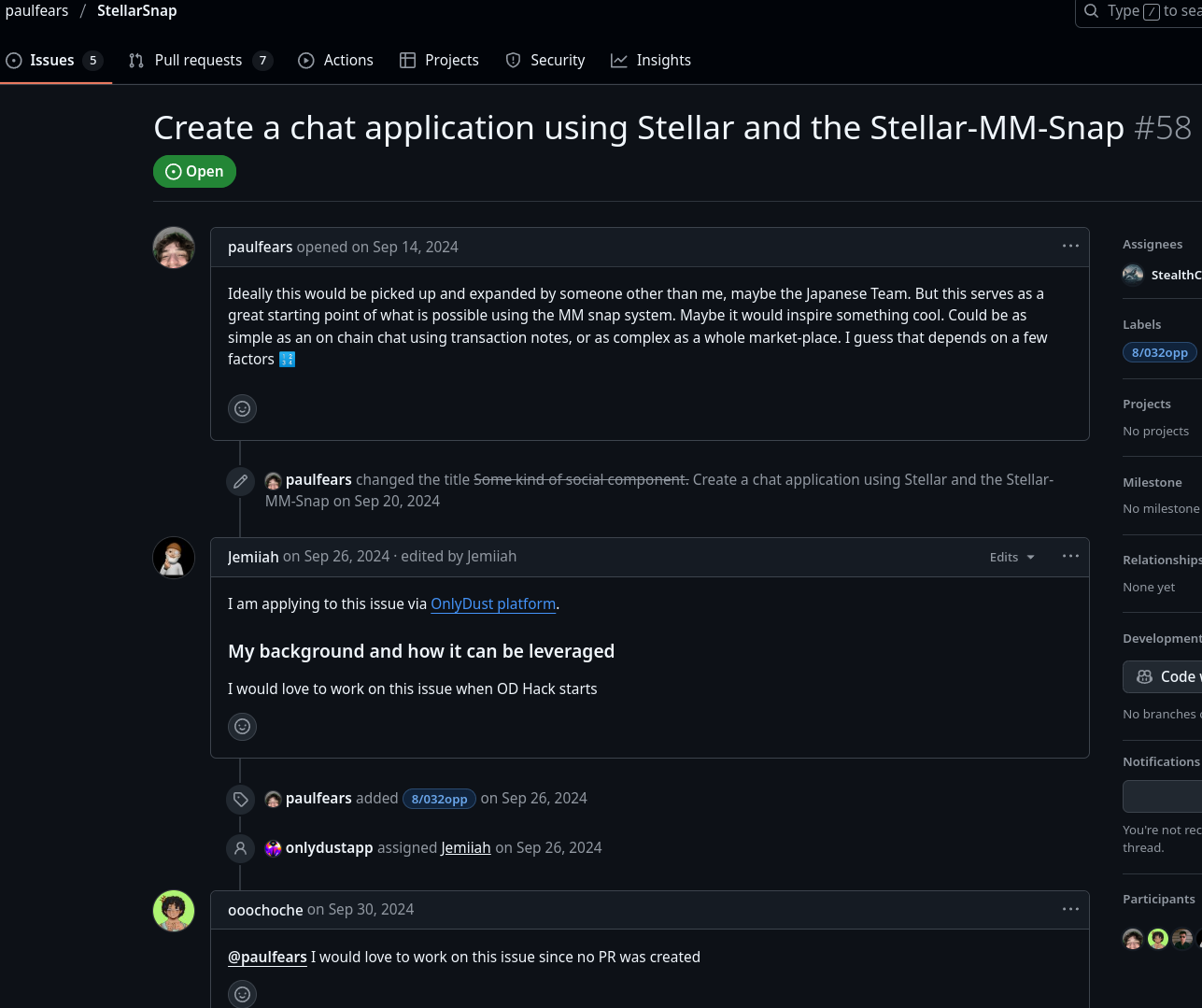
Another reference to the DPRK IT Worker bestselection18 / mymiracle0118
bestselection18 used multiple names (Hiroto Iwaki, Taku Yamamoto) and claimed to be Japanese. This is most likely how he verified himself on OnlyDust; however, we did not receive any confirmation from the company despite multiple requests.

Hiroto Iwaki “real” physical appearance
We decided to take matters into our own hands and began engaging with the DPRK-linked accounts. While conducting parallel investigations, we identified a profile using identities of motokimasuo (now deleted) and kirbyattack (still active), further confirming these accounts are connected and working together. We strongly suspect that bestselection18, motokimasuo and kirbyAttack are the same person working on the mentioned project using multiple identities.
With the sole purpose of confirming that bestselection18 is indeed part of their team, we decided during an interview to ask Motokisauo/kirbyattack to introduce himself in Japanese. However, the candidate’s response was to remove their headset and leave the call, confirming our hypothesis that he is a DPRK IT worker. It made for an extremely awkward conversation you can watch below.
Notice, Motoki is using the same e-mail address truepartner312@gmail.com as address connected to the kirbyAttack actor.
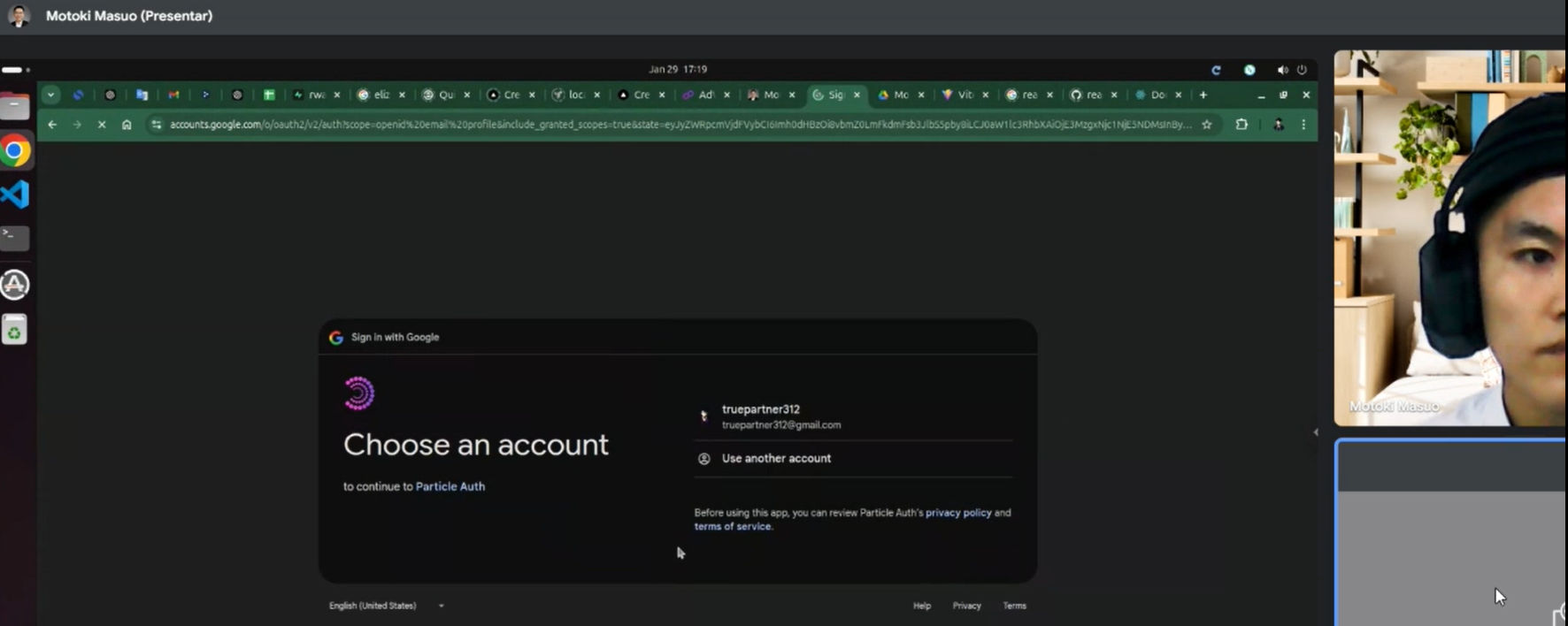
We proved that motokimasuo and kirbyattack accounts are working in coordination with bestselection18. Both accounts are active within the same private repository showcased by Motoki during the call.
Motoki’s poor opsec outting him as the part of the DPRK team operating a scam project, together with bestselection18 and kirbyAttack
Motoki’s official portfolio website

Documents provided as part of the “fake” KYC process we conducted by Motoki
The lesson here is to perform video call verification of ANY remote worker having access to ANY potentially sensitive code (KYC documents are NOT enough). It often doesn’t take much effort, a simple video call that follows up on the actor’s claimed experience (or nationality, as in the case of motokimasuo) can save your company from the DPRK IT Worker threat. We didn’t receive any confirmation from either Stellar or OnlyDust as to the above findings, however, we feel the case is strong enough to classify all of the mentioned actors as North Korean IT Workers. It’s safe to assume that any secrets shared with any of these actors were shared within the internal DPRK team. Similarly, any files or code run by legitimate developers, received from the said actors, should be treated as malicious until proven otherwise.
The Scam Pivot
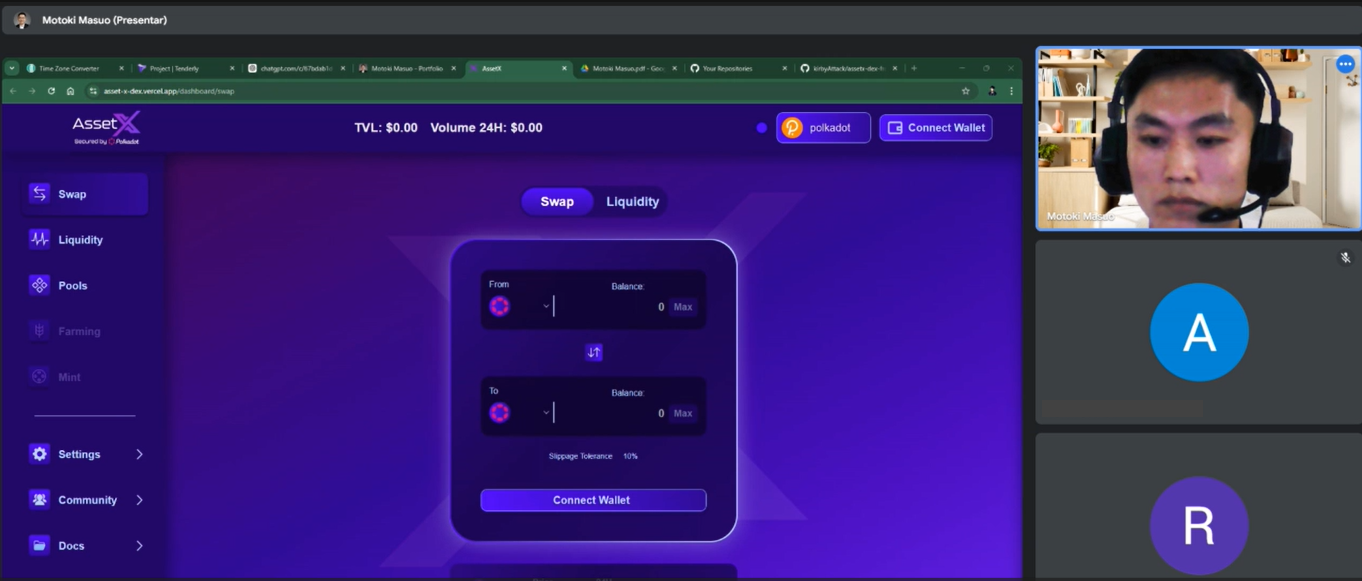
The interesting tidbit from the bestselection18-related cluster is his activity outside of OnlyDust and BuildOnStellar programs. In one of the previous articles, we covered a curious case of NickLFranklin, a persistent DPRK-related threat actor that evaded detection for at least a year while posing as a blockchain security researcher. In the case of NickLFranklin, we unearthed additional connections to different phishing, rugpulls, and scam-like projects outside of his usual malware-delivery activities. The situation is no different with bestselection18 and his network. In May 2024, the merry team of our actors unsuccessfully tried to exploit a Polkadot governance program to fund their platform, potentially a scam, Asset-x. The vote for funding fell through after the community reacted to a massive amount of red flags (anonymous team, bogus background, etc.). It’s worth noting that Asset-x seeded the initial DEX liquidity with 81k USD and asked the Polkadot community for additional $200k USD funding.
Motoki showing front end of now defunct scam project as part of the fake recruitment call we conducted
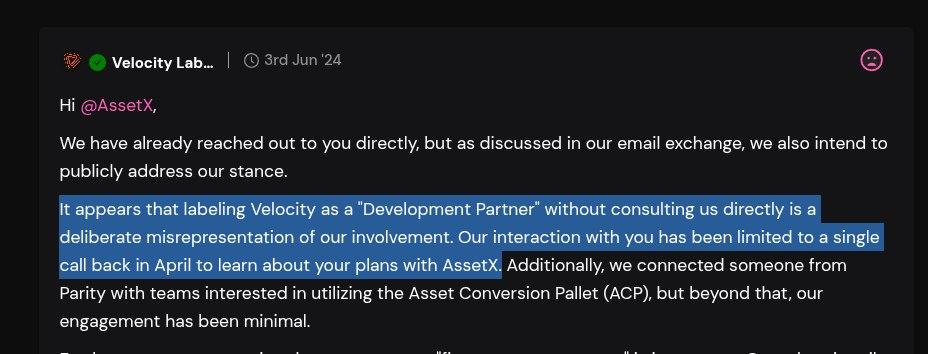
One of the comments about Asset-x proposal for funding. Polkadot community successfully fended off this attempt.
Third Actor and His Two Identities
The last threat actor connected to the onlyDust platform we identified is aidenwong812. This actor was discovered on February 19, and by February 26, while waiting for a message from onlyDust about the previous actors, we independently confirmed the malicious nature of aidenwong812. The company was notified on February 28 about this additional actor; this time, however, aidenwong812 got “spooked” by something and changed his identity on February 26, choosing cryptogru812 as a new handle. aidenwong812 received at least 210USD for his work across four different Starknet-related projects before abruptly removing his identity and traces of payments made from onlyDust (onlyDust billing data seems to be tied directly to the GitHub API-returned username). Then, cryptogru812 returned and continued to get paid, receiving $166 for 9 successful PRs across the same Starknet-related projects. The company did not react to information about cryptogru812 and actor managed to sneak another few Pull Requests as far as into March 14th. As of the time of writing, the actor is still active.
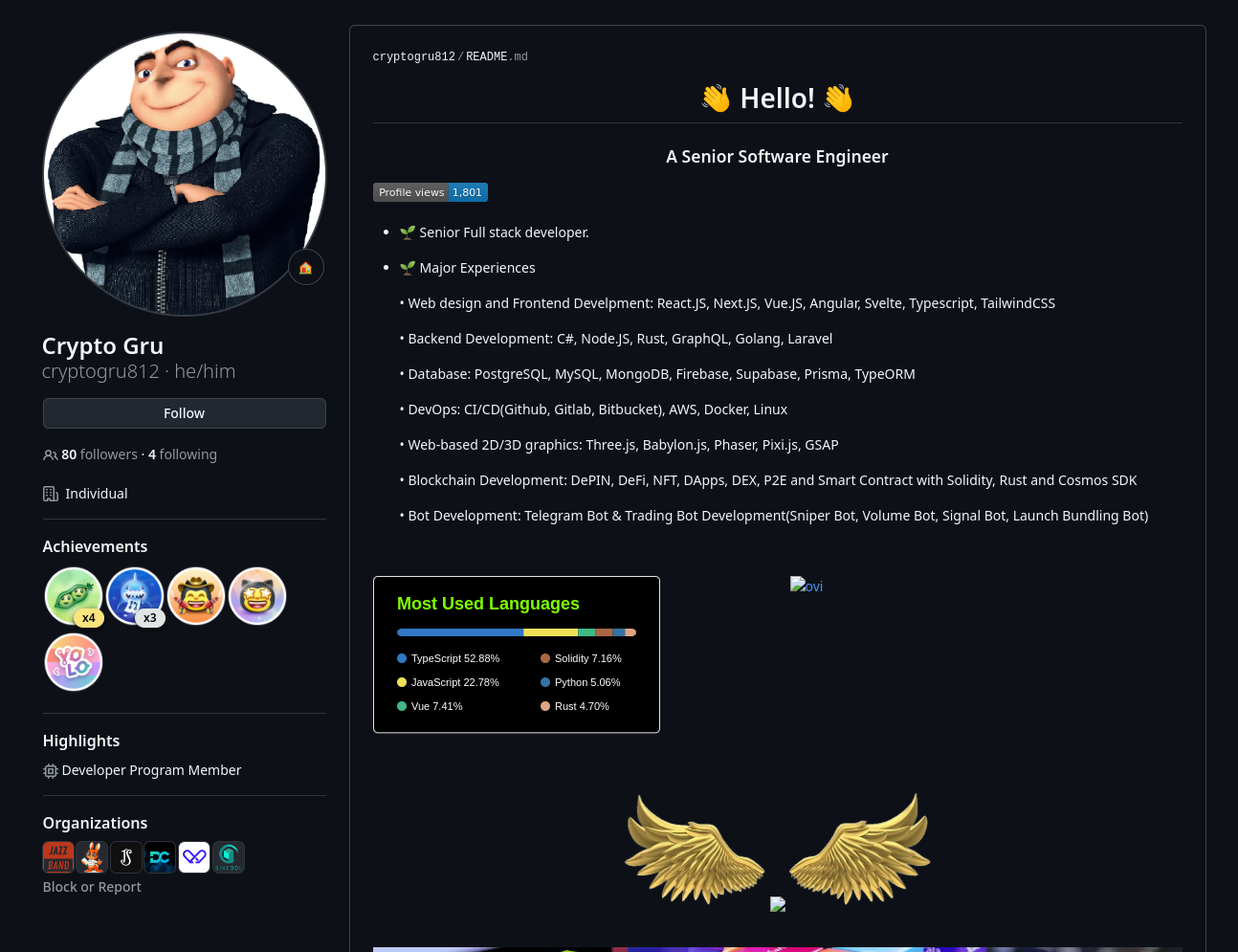
View of cryptogru812 Github account, previously aidenwong812
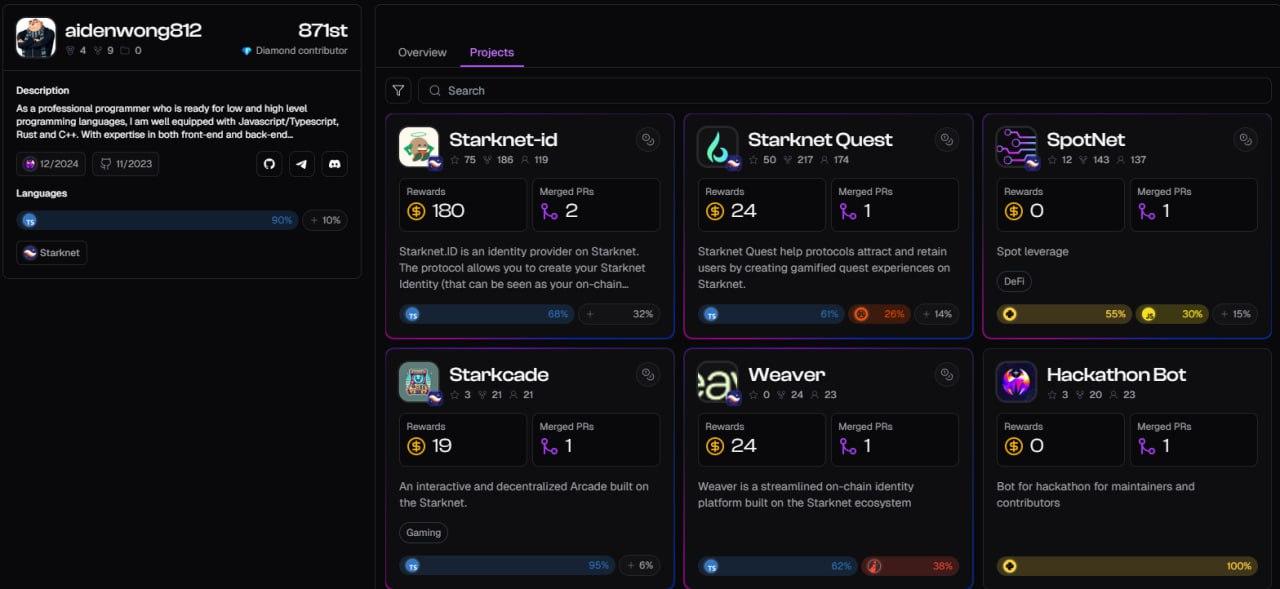
Amounts paid to the DPRK IT Worker aidenwong812 by onlyDust, before nickname change
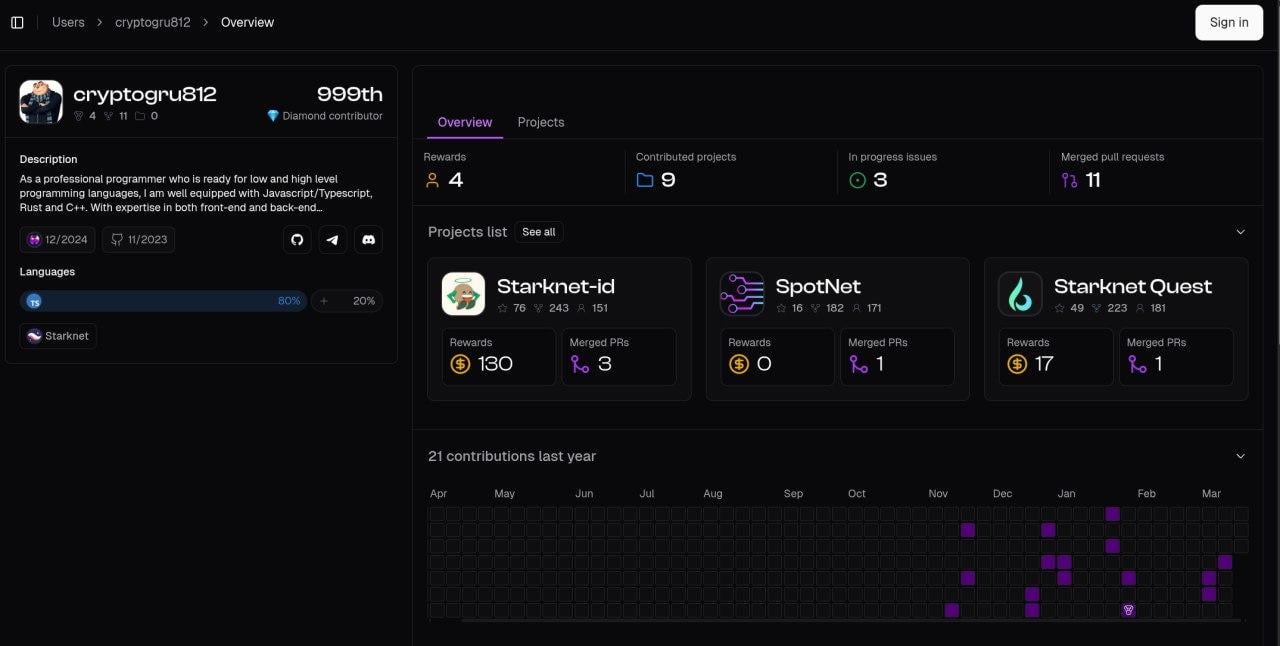
Amount paid to the DPRK IT Worker cryptogru812 by onlyDust, after nickname change and after our initial report
cryptogru812 / aidenwong812 was the most developed DPRK IT Worker personality out of the three. He is connected to many different suspicious accounts and is running multiple IT Worker-related campaigns.
List of highly unusual patterns discovered:
-
Identity rotation on GitHub:
- In the case of
aidenwong812, we were able to discover multiple identities used:wongaiden812@gmail.com : aidenwong812 / Aiden WongDELETED / DEAD (February 26, 2025)vincenzagiorgi6@gmail.com : Ruslan Vinnichuk / RuslanDELETED / DEADpwlkjakub@gmail.com : Ruslan Vinnichuk / V0410 / Yehor / aidenwong812DELETED / DEADgru.dev259007@gmail.com : V0410ACTIVE
- Each of the above identities has its own history of activity. Notice
pwlkjakub@gmail.comusing all of the mentioned identities, indicating all credentials were used by the same person, who was also trying to obscure this fact. -
V0410is another suspicious actor. We managed to establish a strong connection withaidenwong812through:- Re-use of the same avatar picture on the personal website of
aidenwong812and on theV0410GitHub profile.
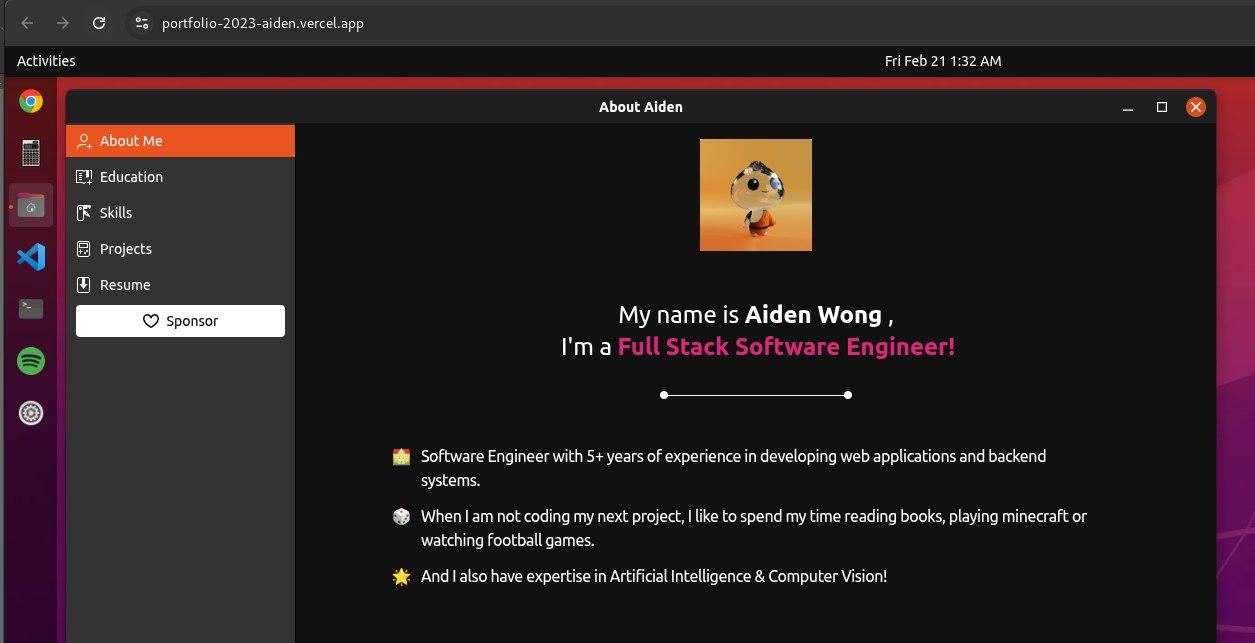
Aiden Wong’s personal website
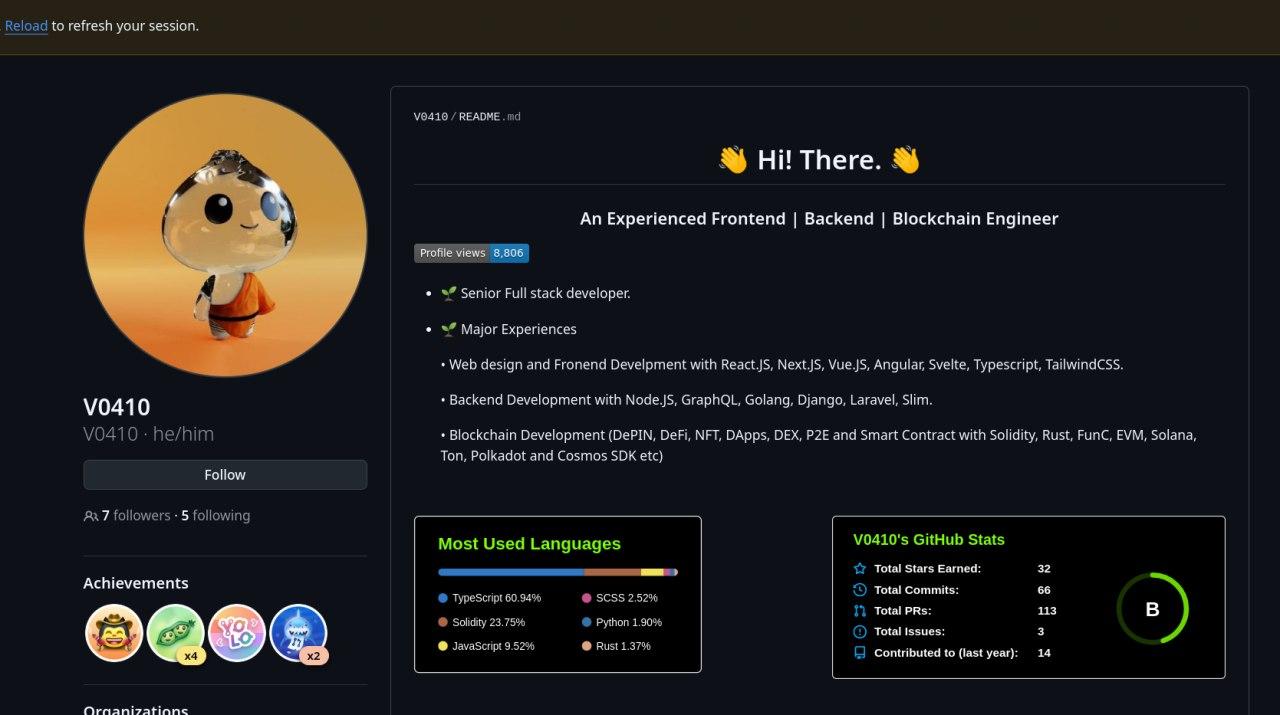
V0410, a different identity of Aiden Wong, website
- Re-use of the same avatar picture on the personal website of
-
Git commit history clearly points to different actors cooperating to apply for different jobs across Web3.
- Example: Application to
nodeguardians.iolast year.V0410- https://github.com/V0410/ng-frontend-application/commits/main/aidenwong812- https://github.com/aidenwong812/ng-frontend-application- Timestamp analysis is interesting: both repositories were updated at almost exactly the same time (a 10-minute difference), indicating a “team effort” for this job application.
- Example: Application to
- Connection to other suspicious actors:
V0410:- We did a full GitHub profile analysis of this username, discovering exactly the same
nameandemailGit credentials as used byaidenwong812; however, there are a few notable differences:vincenzagiorgi6@gmail.com : Maksym Poplavskyi- notice the same email was used with a different name on theaidenwong812account.Maksym Poplavskyiidentity is DELETED.- A person of this name (a Ukrainian name, a choice we observe being popular with DPRK actors) is active on the Fiverr and LinkedIn platforms:
vincenzagiorgi6@gmail.com : V0410
- There are more significant connections between few other distant actors, which are not relevant at this time to the Starknet x OnlyDust investigation. We will not dig deep into the history of the accounts below, but every single one “cross-contributes” between repositories and fits the usual DPRK IT Worker pattern:
lionstar259007: aidenwong812/tomi-runner/commit/23007375acb432a6aa318a79b8fb06fd8a229c29hi-tech-AI: aidenwong812/MATTER_UI/commit/2b03491baec442162cde7cca5f2b7286b06b9146brightlystar0117: aidenwong812/Polkadot-hydration-Cross_chain-Defi/commit/9562b9a7bb17488ac8203c66410e295f800a13ebImfanAi: aidenwong812/chicken-game/commit/63155ca917d07758c18cd270782c7d6219a4eae7techeng322: aidenwong812/MATTER_UI/commit/376dfa583a19a578974f4779fb6a8975b2a204fe
- We did a full GitHub profile analysis of this username, discovering exactly the same
- “Minion” avatar: This is something we discovered in past investigations. Certain “fake” accounts have a particular affinity for specific avatars. In the case of previous DPRK/insider threats, we often observed “minion” avatars from the 2015 cartoon series.
aidenwong812’s avatar reflects this pattern. Moreover, accounts associated with him (e.g.,lionstar259007) also follow this pattern. - Spam issues/comments opened in at least one suspicious organization associated with “Account Farming” that we were already tracking.
- For the claimed experience and amount of activity on GitHub,
aidenwong812’s command ofgitis suspiciously subpar. This is something we often observe with DPRK IT Workers, where they over-commit changes, do not use.gitignore, do not fork but git clone the whole code, and push it to their GitHub with public visibility. - Identity changed again on February 26, 2025, to
cryptogru812.
- In the case of
aidenwong812 / cryptogru812 operates so many different identities that he often confuses his Ukrainian fake identity on Linkedin, with his old Italian identity on Github only to re-emerge as a Chinese/Korean Web3 developer. A real mix.
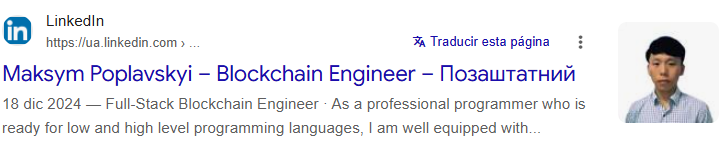
Cached view of Aiden Wong linkedin, still using old identity of Maksym Poplavskyi
List of Affected Projects and Developers
We have no knowledge whether OnlyDust ever contacted the affected developers with any of the above information. Because some public interactions between developers and DPRK IT Workers suggest the existence of communication channels other than just the public GitHub Issues, we feel it is important to warn the public and inform all potentially affected parties about the nature of their “co-workers”. It is always possible that some malicious payload was handled on private communication channels, even if the code pushed by the North Koreans doesn’t seem to be malicious.
0xExp-po- https://github.com/tupui/soroban-versioning (Project is part of a BuildOnStellar grant)
- Amount received / Successful Pull Requests:
- $200
- 26 Pull Requests Merged
bestselection18- onlyDust x Stellar projects (displayed through the onlyDust UI)
- https://app.onlydust.com/projects/trustless-work-/overview (Stellar)
- https://app.onlydust.com/projects/spotnet/overview (Starknet)
- https://app.onlydust.com/projects/stellar-wallet/overview (Stellar)
- https://communityfund.stellar.org/dashboard/submissions/reccBR6CyNvbjqL2E (Stellar) Project awarded 71,000 USD — to develop “The Stellar Integration on MetaMask”
- https://app.onlydust.com/projects/tansu/contributors (Stellar)
- Amount received / Successful Pull Requests:
- Trustless-work - $590
- Stellar-Wallet - $510
- Tansu - $180
- Spotnet - $0 (according to the onlyDust UI; however, the actor successfully merged a single PR)
- 18 Pull Requests Merged
aidenwong812/cryptogru812- All projects are Starknet related
- https://app.onlydust.com/projects/starknet-id
- https://app.onlydust.com/projects/starknet-quest
- https://app.onlydust.com/projects/spotnet
- https://app.onlydust.com/projects/hackathon-bot
- https://app.onlydust.com/projects/starkcade
- https://app.onlydust.com/projects/weaver
- Amounts received:
- For
aidenwong812:- Starknet-id - $180
- Starknet Quest - $24
- Starkcade - $19
- Weaver - $24
- Spotnet - $0 (successful PR merged)
- Hackathon Bot - $0 (successful PR merged)
- We’ve lost the exact amount of Pull Requests merged because actor wiped his profile, at least 7 Pull Requests Merged
- For
cryptogru812:- Starknet-id - $130
- Starknet Quest - $17
- Spotnet - $0 (successful PR merged)
- 11 Pull Requests Merged
- For
In total, we confirmed at least 1874 USD paid to the above three actors, the amount may be higher as we have no knolwedge how exactly onlyDust settles payments for contributors. It’s worth noting that some projects affected are recipents of considerable grants between 50,000 to 80,000 USD. Additionally, 62 Pull Requests were added by the North Korean developers to 11 different repositories across the onlyDust ecosystem. On top off it, few other, external to onlyDust projects were affected. The scope of impacts is big and all affected parties are urged to review their code as well as personal hardware for signs of compromise. We would also like to urge other onlyDust developers and users to reflect back if interactions with any suspicious contributor took place and report it to us or the company.
PSA for Bounty, Freelance and OSS Projects
The amounts of money paid to North Koreans in this particular instance are not high. In many cases, when a DPRK IT Worker gets on the payroll, he immediately attempts to cash out as much as $10,000 to $20,000 USD per month of work. However, in the case of onlyDust, the risks are spread over a different surface:
- Risks to open source projects and their maintainers: DPRK IT Workers often work closely with DPRK Hacking Teams. We frequently observe crossover with campaigns like “Contagious Interview”, where the DPRK IT Worker serves as an entry point to deliver a malicious payload to an established contact - in this case, maintainers of projects hosted on OnlyDust, grant operators, funding teams.
- Credibility boosting: The DPRK IT Worker will use the farmed commits and rank gained on platforms like OnlyDust in his next attempts at getting hired, potentially onto a payroll at a regular company. This time, he will have a more credible-looking portfolio than one with just “faked” commits.
- Scoping the ecosystem: Effectively, DPRK IT Workers filter relevant information about future hacking activities back to the DPRK Hacking Team. The interesting aspect of the onlyDust case is the actors heavy focus on the Starknet/Cairo ecosystem. It’s a more niche development environment than EVM or Solana, but in recent months, a few Starknet projects have been successfully attacked, and a few other attempts by North Koreans to gain access to this particular ecosystem have been spotted.
To summarize, DPRK IT worker threats do not happen in isolation. When discovered, it usually affects a lot of parties. North Koreans are extremely persistent in trying to establish contact and they’ll leverage any crumbs of credibility gained. Even if seemingly benign, the moment will come when a malicious dependency is injected into the code, a backdoor is installed, or all of the legitimate developer teams interacting with the DPRK will receive one of the popular infostealers through a private channel of communication. You, your project, or your investors may be changed into a part of a supply chain attack. The best defense is vetting your remote workers, following up on any suspicious behavior and inconsistencies in communication, and issuing notifications to all potentially affected parties.
Treat this seriously. You are putting the whole developers ecosystems at risk.
IOCs
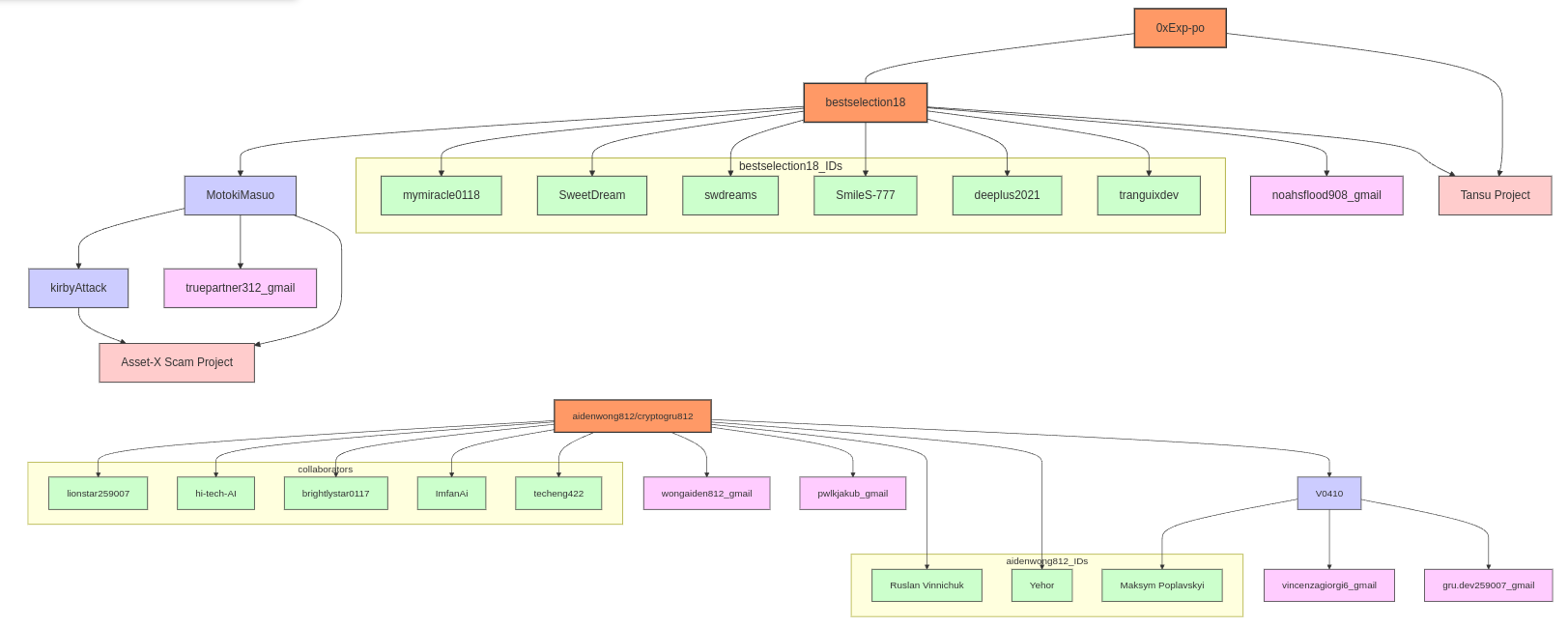
Visualization of connection between the all actors discussed
GitHub Profiles
https://github.com/SweetDreamhttps://github.com/SmileS-777https://github.com/StealthCoder1109https://github.com/V0410https://github.com/ImfanAihttps://github.com/aidenwong812https://github.com/brightlystar0117https://github.com/bestselection18https://github.com/codeperthttps://github.com/cryptogru812https://github.com/deeplus2021https://github.com/hi-tech-AIhttps://github.com/kirbyAttackhttps://github.com/legendx0333https://github.com/lionstar259007https://github.com/motokimasuohttps://github.com/mymiracle0118https://github.com/swdreamshttps://github.com/toptalhookhttps://github.com/techeng322https://github.com/tranguixdevhttps://github.com/billiedoxhttps://github.com/deeplus2021
Email Addresses
lucaschang1127@gmail.comxtinc.exp@gmail.comnoahsflood908@gmail.comtruepartner312@gmail.commotokimasuo89@gmail.comwongaiden812@gmail.comvincenzagiorgi6@gmail.compwlkjakub@gmail.comgru.dev259007@gmail.comtoptall.cook@gmail.comkallis0312@gmail.comtakutic.tech518@gmail.comwilliamduncan91413@gmail.com
Identities
Lucas ChangHiroto IwakiTaku YamamotoMotoki MasuoAiden WongRuslan VinnichukMaksym PoplavskyiSerhii MinchevDanylo NarizhyiTakuma KijimaAntonio RomeroJacob ChanEdgar RavelinoEmesto SantosJulio AcinNil ArandaTheodore FernYamataku HaraWilliam DuncanHenry Hale
Payroll
- None, please direct your queries to onlyDust, Build on Stellar and Starknet programs mentioned earlier.