Following Nisos recent publication on North Korean IT worker operations, we had a feeling more can be extracted from this data and performed the usual deep OSINT scan using our software. Accounts linked to the operation revealed unexpected connections to Russian military imagery.
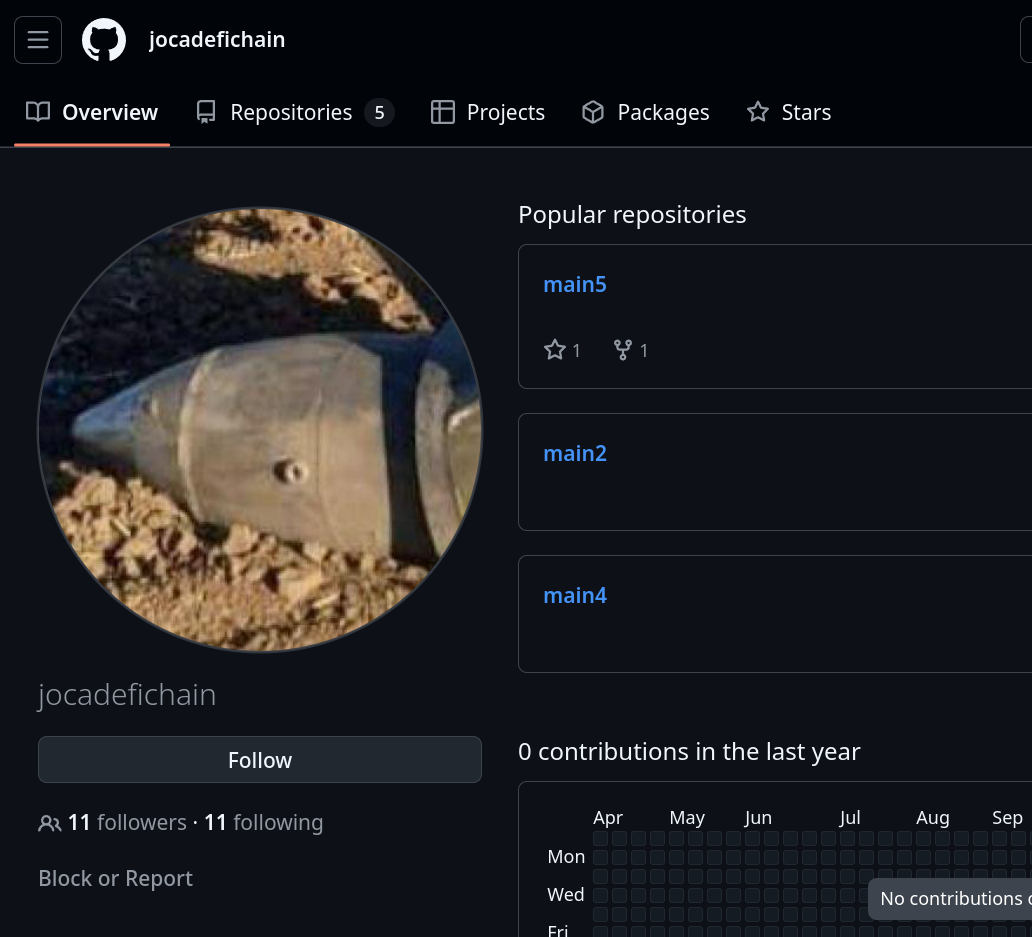
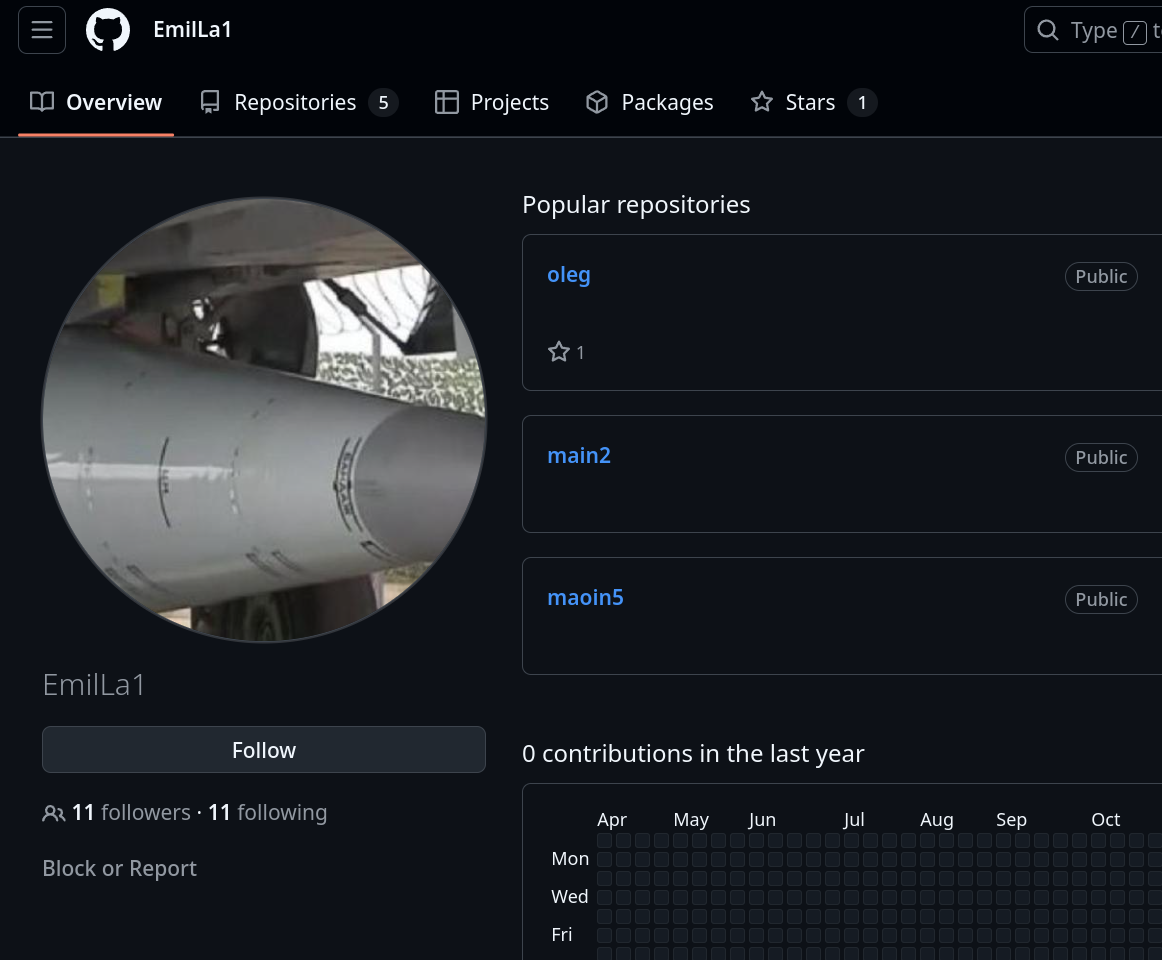
Initially, Nisos flagged and confirmed three GitHub accounts as related to North Korean IT workers (imcode65, kanbei0605 and code-0605). We uncovered additional actors connected to above three identities. Two of those actors (jocadefichain and EmiLa1) featured profile pictures distinctly out of pattern with typical DPRK operational security. Rather than using generic AI-generated avatars, these accounts displayed images related to Kinzhal hypersonic missiles - Russia’s advanced weapons system that has been deployed in Ukraine.
Russian Military Connection
The profile images were traced to specific Russian sources:
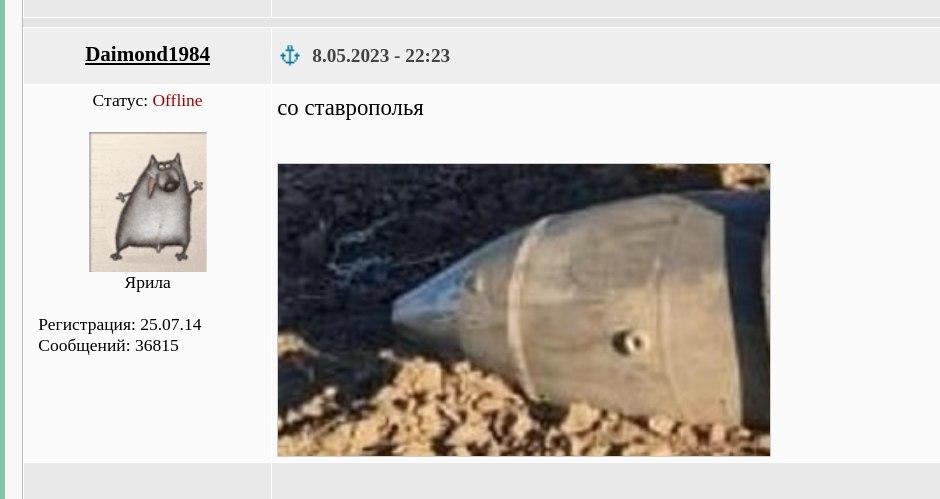
- One image originated from a Russian forum topic titled “USA is almost sure that UA Armed Forces took down Kinzhal over Kyiv”, where one of users provided a picture of an unidentified missile crashed near Stavropol, Russia.
- The second image was sourced from Russia-1 state television, however, the resolution of image used on Github differs from the resolution in the source image, suggesting the avatar image was “screen captured” from some other device.

Notably, Stavropol hosts Russia’s 49th Combined Arms Army of the Southern Military District, which has been involved in operations against Ukraine’s Kherson region. The city is also a known operational center for GRU (Russian military intelligence) activities.
What’s odd is that both images are “dated” and weren’t a part of any broad media campaign. The Stavropol reference comes from 2023, while the Kinzhal image is from 2019 TV coverage of Putin’s visit to the base where Kinzhal was presented to him.
Implications
The evidence suggests these operators are consuming niche Russian military content rather than mainstream Western media, indicating their geographical and ideological positioning. It’s also the first time we encounter such specific choice of an avatar, as in most cases, these are generic. No other accounts within this cluster used any image of such type.
This finding adds to growing evidence of deepening Russia-DPRK cooperation beyond conventional military aid, potentially extending into the cyber domain with shared personnel or operational protocols.
Cluster information
All of the below accounts are high confidence DPRK IT Worker actors connected to the Nisos discovered cluster. Accounts are currently not operational.
What’s interesting is all accounts share the same “empty” repositories, following the same naming scheme of main, main1, main2, main3, etc. Those appear to be created manually as some typos can be spotted, like mina5 or miamn2. Similarly, all accounts follow each other and ocassionally star each others repositories.
In one instance, the account using Russian military imagery breaks away from the main[0-9] naming scheme and hosts an additional repository named oleg.
It’s also worth noting that no e-mail addresses were found, but chosen GitHub names indicate impersonation efforts.
IOCs
github_url, github_name, created_at
https://github.com/EmilLa1 : AlexHarper1 : 2022-10-25T08:31:22Z
https://github.com/RomanHarazha : RaymondPayne1 : 2022-10-25T08:41:27Z
https://github.com/ThePinion : Richard0Gibson : 2022-10-25T14:50:43Z
https://github.com/girlbuzz : MelvinAllen : 2022-10-25T19:47:28Z
https://github.com/itayplav : EduardoLunaq : 2022-10-25T20:04:05Z
https://github.com/SeanJones11 : SeanJones11 : 2022-10-25T20:27:17Z
https://github.com/belbazanas : freedgregory : 2023-01-31T01:01:13Z
https://github.com/jocadefichain : leroma1 : 2023-02-13T18:46:42Z
https://github.com/cristttt : cristttt : 2023-05-18T21:13:43Z
https://github.com/eddieda1 : eddieda1 : 2023-05-18T21:18:12Z
https://github.com/shanelka-here : georgeee12 : 2023-05-18T21:23:29Z

